How to Deploy and configure DNS 2016 – (Part1)

DNS stands for Domain Name System whose main job is to translate domain names like
http://www.google.com to IP addresses. When a user enters http://www.google.com into the
browser, his computer will send out query to ask its DNS what the corresponding IP
addresses is. And the DNS will search from its local cache or if it cannot find, it will
make recurring query to higher DNS servers until the IP is found. Finally it will send
back its response. Therefore, the DNS plays a very critical role in the Internet structure.
I have 2 servers DC01 and DC02. DC01 is my domain controller which has DNS installed (Active Directory Integrated) and DC02 will be my standalone DNS server.
Now installing DNS can be done in one of several ways. It’s a role, so of course we can use Server Manager for this, bring up Server Manager, and to install a role you can go to Manage, Add Roles and Features, walk through the wizard accepting the defaults and when you come to the Select Server Roles you will find DNS in the list.
One of the things that’s very common is that when you have a domain controller, and Active Directory is installed, you also install DNS with it because there are Active Directory zones that get created and that’s one of the things we want to look at. This is my DC01

Another way to install this is by using the PowerShell commandlets and once again, to find the feature, WindowsFeature, you can just search for DNS and you’ll see that you’ll get DNS and the RSAT tools for DNS. (This is done on my second server DC02 which is not a Domain Controller)
Install-WindowsFeature -Name DNS -IncludeManagementTools


Now to verify it we can run Get-WindowsFeature DNS

We have commandlets that we can manage all the aspects of DNS, so I’m going to be showing you how to do things graphically, but I want you to keep in mind you can do this, get-help, and all of the commandlets for DNS, the nouns of the verb noun combination has been prefixed with DNS, so to find them I’m going to do -DNS and that’ll keep the list shorter and find all of those commandlets to get and set different things and remove things, if you’d like, from DNS and all the different options.
Now once the DNS has been installed and the management tools have been installed you can start to work with DNS. Now you can get to the management tool from Server Manager and go to Tools and go to DNS and that’s the name of the management tool or you can run this command in Powershell to open DNS Manager Dnsmgmt

Powershell

Now that we have this graphical, we’re ready to start to take a look at all the different zones and the different things that we can do with DNS.
OBS!!! Remember that I have 2 servers. DC01 is my domain controller and we will start from there because I want to start off by showing you a particular type and that would be Active Directory integrated. (To install Active Directory with DNS please check How to Install and configure Active Directory Domain Services 2016
DC01
Run Server Manager –> Manage –> Tools –> DNS.

Before we start let’s define what DNS Zone means.
DNS Zone hold the data needed by dns to operate.
A zone file contains the data for a portion of the DNS Name space. For this reason, zones allow different administrators to have control over that part of the DNS name space. Depending on what type of zone file that you create, this will determine what types of DNS records can be stored in that zone and if the data in that zone can be modified.
We’re going to start with the Forward Lookup Zones and because mine is on a domain controller there’s already some zones that exist out there. Forward Lookup Zones is, well, what you would think of as far as the typical name resolution. It’s going to resolve a name to an IP address. Reverse Lookup Zones resolve the backwards, the other way, from an IP address to a name, so if you kind of think of it this way maybe I know somebodies IP address, and I don’t know who they are and I’d like to find out, I can ask using a Reverse Lookup Zone.
We will take a look on Reverse Lookup Zones, Trust Points and Conditional Forwarders in different part.
_msdcs.mehic.se folder which is know as Microsoft domain controller service contains srv records which is used for locating domain controller for their services. It contains generic srv records, ldap records,Kpass records, CNAME etc

My domain is Mehic.se and you can see that I have over here to the right a bunch of A records.

Now this is very important when it comes to Active Directory because we have things under here called SRV records and they help us find domain controllers and global catalog servers so that we can do authentication and authorization. If you open for example _tcp you will find SRV records.


Let’s explore properties of the zone. Right-click on your zone (mehic.se in my case) and select Properties

Zone Properties window will pop-up.
GENERAL TAB
It says here on the General tab that it’s running, which means it can answer queries, and the type is Active Directory Integrated and here’s what Active Directory Integrated means. I’m going to show you the different zone types primary, secondary, and stub zones. Those zones, except for secondary’s, can be Active Directory Integrated and what that means is is that the zone is going to be stored in an application partition in Active Directory. That is the benefit you get. On DC that have DNS it can get that zone information, so it acts like fault tolerance. It’s important just to note that Active Directory Integrated means all those A records, and whatever we create in that zone, is stored in Active Directory and will get replicated to other domain controllers.

Replication: All DNS Servers in this domain ( Now when we are Active Directory Integrated we can choose who we’re going to replicate that information to)
If you click on Change button you will get option to replicate to all DNS running on DCs in this Forest, all DNS running on DCs in domain (which is default) and to all DCs in domain, so you can control the replication of where this gets copied and who has this for fault tolerance.

Dynamic Updates (Secure Only) – what this means is is that clients that have authenticated can update their DNS records, and this is the option you get on Active Directory Integrated zones. We do have some other options that I’m going to show you, Nonsecure and secure, and None as we create our own zones.

Aging/Scavenging – These features are provided as a mechanism for performing cleanup and removal of stale resource records, which can accumulate in zone data over time. (We will take a look on this later.)
START OF AUTHORITY (SOA) TAB

Serial Number: indicates the version of the DNS database files. The number is updated automatically whenever you make changes to zone files.
Primary Server: The host that is storing the primary zone file.
Responsible Person: The e-mail address of the person responsible for administering the domain’s zone file. You should note that a “.” is used instead of an “@” in the e-mail name.
Refresh Interval: The interval at which a secondary server checks for zone updates
Retry Interval: The time, in seconds, a secondary server will wait before retrying a failed zone transfer.
Expires After: The time, in seconds, that a secondary server will continue to attempt to successfully complete a zone transfer from the primary DNS server. I
Minimum (Default) TTL: The minimum time-to-live value applied to all resource records in the zone file.
TTL For This Record: The time-to-live value for this SOA record itself.
NAME SERVERS TAB
Here we can add secondary servers for our existing zones to the name server (NS) record to make them authoritative for the zone. Typically, it may be necessary to perform this procedure at the primary zone only when you add Domain Name System (DNS) servers to act as secondary servers.

WINS TAB
On this tab you can configure WINS to resolve names which are not found by querying the DNS namespace.

ZONE TRANSFERS TAB

The “Zone Transfers” tab has a checkbox to allow zone transfers to other DNS servers with 3 options. You can specify any server, only to those listed in the Name Servers tab, or to specific servers by entering their IP addresses. I didn’t configure this so if I try to request content of this zone via powershell I will receive an “error”

If I enable it and choose for example To any server, this time I will be able to see content

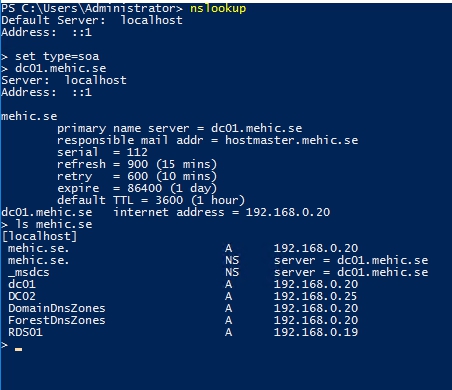
We will come to this later.
SECURITY TAB
When you create an Active Directory-integrated zone, the properties of that zone display a security tab. That tab allows you to set permissions on the zone, similar to setting permissions on other objects in Active Directory. For example, you can explicitly deny users of some lesser-trusted groups access to the zone data entirely, while making other groups read-only for the zone data.

What we covered.
- What is DNS and how to install it (Standalone vs AD Integrated)
- Advantages of Integrated Zones (Replication, Security, Redundancy)
- Properties of the Zone
In the next part we will take a look at creating our own zones, both Active Directory Integrated and not Active Directory Integrated and the different types that we have.


No comments:
Post a Comment